
Monday Aug 22, 2022
#92 - Updating the Executive Leadership Team on Cyber
Show Notes
Hello, and welcome to another episode of CISO Tradecraft -- the podcast that provides you with the information, knowledge, and wisdom to be a more effective cyber security leader. My name is G. Mark Hardy, and today we're going to offer tips and tools for briefing your executive leadership team, including the four major topics that you need to cover. As always, please follow us on LinkedIn, and make sure you subscribe so you can always get the latest updates.
Imagine you have been in your role as the Chief Information Security Officer for a while and it is now time to perform your annual brief to the Executive Leadership Team. What should you talk about? How do you give high level strategic presentations in a way that provides value to executives like the CEO, the CIO, the CFO, and the Chief Legal Officer?
- Story about Kim Jones at Vantiv – things have changed
Let's first talk about how you make someone satisfied -- in this case your executives.
Fredrick Herzberg (1923-2000) introduced Motivator-Hygiene theory, which was somewhat like Maslow's hierarchy of needs, but focused more on work, not life in general.
What a hygiene factor basically means is people will be dissatisfied if something is NOT there but won't be motivated if that thing IS there, e.g., toilet paper in employee bathroom.
Or, said more concisely, satisfaction and dissatisfaction are not opposites. The opposite of Satisfaction is No Satisfaction. The opposite of Dissatisfaction is No Dissatisfaction.
According to Herzberg, the factors leading to job satisfaction are "separate and distinct from those that lead to job dissatisfaction."
For example, if you have a hostile work environment, giving someone a promotion will not make him or her satisfied.
So, what makes someone satisfied or dissatisfied?
Factors for Satisfaction
- Achievement
- Recognition
- The work itself
- Responsibility
- Advancement
- Growth
Factors for Dissatisfaction
- Company policies
- Supervision
- Relationship with supervisor and peers
- Work conditions
- Salary
- Status
- Security
So, what will make a board member satisfied? Today, cyber security IS a board-level concern. In the past, IT really was only an issue if something didn't work right – a hygiene problem. If we learn from Herzberg, we may not be able to make the board satisfied with the state of IT security, but we can try to ensure they are not dissatisfied. Hopefully you now have context for what might otherwise be considered splitting hairs on terminology – essentially, we want our executive audience to not think negatively of your IT security program and how you lead it.
Remember, boards of directors generally come from a non-IT backgrounds . According to the 2021 U.S. Spencer Stuart Board Index, of the nearly 500 independent directors who joined S&P 500 boards in 2021, less than 4% have experience leading cybersecurity, IT, software engineering, or data analytics teams. And that 4% is mostly confined to tech-centric companies or businesses facing regulatory scrutiny.
So, there is essentially a mismatch between a board member's background and a CISO's background. That extends to your choice of language and terminology as well. Never go geeky with your executives – unless you have the rare situation where your entire leadership team are all IT savvy. Otherwise, you will tune them out by talking about bits and bytes and packets and statistics.
Instead, communicate by telling stories – show how other companies in similar industries have encountered security issues and what they did about them (either successfully or unsuccessfully). Show how your cybersecurity initiatives and efforts reduce multiple forms of risk: financial risk, reputational risk, regulatory risk, legal risk, operational risk, and strategic risk. You can show that the threat landscape has changed – nation states and organized crime has supplanted lone hackers and disgruntled employees as the major threats . Regulatory environment changes such as the California Consumer Privacy Act (CCPA) and ultimately the follow-on legislation from 49 other states will impact strategic business planning. Show your board how to avoid running afoul of these emerging requirements. And, of course, there is the ever-present threat of ransomware, which has evolved from denial-of-access attacks to loss of customer and internal data confidentiality. That threat requires top-level policy and response plans in advance of an incident -- it's too late to be making things up as you go along.
Now, before we go into the Four Major Topics executives need to hear (after all, that's what I promised at the beginning of the show), let's ask, "Why are we briefing executives on our cyber program?" Any company that is publicly traded falls under the scope of the Securities and Exchange Commission or SEC.
The SEC has published Cybersecurity Guidance that offers suggestions for investment companies and investment advisors. They recommend investment firms "create a strategy that is designed to prevent, detect, and respond to cybersecurity threats".
The creation of a security strategy and education of employees on the strategy is at the core of what CISOs do. So, a translation of the SEC's guidance is to hire a CISO, have that individual create and execute a cybersecurity strategy. In fact, the SEC's quote above calls out three of the Five Functions of the NIST Cybersecurity Framework which are: (1) identify, (2) protect (prevent), (3) detect, (4) respond, and (5) recover.
Our second question is, how often should we be updating the Executive leadership team? Since the SEC requires companies to disclose risks in their 10-K statements on a yearly basis then you should be briefing cyber updates to the Executive Leadership team at least on an annual basis. We recommend quarterly or semi-annual updates to give more touch points on important topics. You can draw parallels to quarterly financial statements.
Let's say the Risk Committee chaired by the CEO has agreed to hear the status of the Cyber Program twice a year. What should we brief the executive leadership team?
Let's look at what's required by law.
The State of New York requires financial services organizations to follow New York Department of Financial Services (NYDFS) regulations. Section 500.04 provides additional information about CISOs. It states:
Each Covered Entity shall designate a qualified individual responsible for overseeing and implementing the Covered Entity's cybersecurity program and enforcing its cybersecurity policy (for purposes of this Part, "Chief Information Security Officer" or "CISO").
The regulations also state:
The CISO of each Covered Entity shall report in writing at least annually to the Covered Entity's board of directors or equivalent governing body. If no such board of directors or equivalent governing body exists, such report shall be timely presented to a Senior Officer of the Covered Entity responsible for the Covered Entity's cybersecurity program. The CISO shall report on the Covered Entity's cybersecurity program and material cybersecurity risks.
These types of requirements aren't confined to Wall Street. The Bermuda Monetary Authority requires insurance companies to follow their Cyber Risk Management Code of Conduct. It states that:
The board of directors and senior management team must have oversight of cyber risks. The board of directors must approve a cyber risk policy document at least on an annual basis.
So, both the State of New York and the Bermuda Monetary Authority want CISOs to provide risk management and perform at least yearly reporting on material cyber security risks. Many more regulatory bodies do; these are just offered as examples.
If you are going to function effectively as a leader, you should find some way to create a win-win from most any situation. You likely have a regulatory requirement to brief your board or leadership on a periodic basis. That's fine. But have you ever asked yourself, what do I want in return?
Hmm.
What you want is for your board to set the security culture from the top. Boards hold senior leadership (think C-level executives) accountable, and you want the board to ensure the CEO makes cybersecurity a priority for the organization. ISO 27001 has a nice tool – the Information Security Management System (ISMS) Policy Statement – which is senior leadership's declaration of the importance of cybersecurity within the organization.
One example I found is that of GS1 India, a standards organization that helps Indian industry align with global best practices. Their ISMS Policy statement begins with:
The Management of GS1 India recognizes the importance of developing and implementing an Information Security Management System (ISMS) and considers security of information and related assets as fundamental for the successful business operation. Therefore, GS1 India is committed towards securing the Confidentiality, Integrity, and availability of information for the day-to-day business and operations.
If you can get a formal declaration of support from the top, your job is going to be a whole lot better. Otherwise, you might just end up being the Chief Scapegoat Officer.
Now let's define the four things that an executive leadership team should hear from their security leader that will convey the message that you have a handle on your scope of authority and are executing your responsibilities correctly. Those four focuses are:
- Cyber Risks and Responses
- Cyber Metrics
- A Cyber Roadmap that Identifies High Profile Programs and Projects
- Cyber Maturity Assessment
Let's dig in. With respect to "cyber risks and responses," create a slide for executives that shows the top cyber risks. Examples may include things like ransomware, business email compromise, phishing attacks, supply chain attacks, third party compromise, and data privacy issues.
As a practical matter when briefing cyber risks, never just share a risk and walk away. Executives hate that. Be sure to talk about what you are doing as a CISO to mitigate this risk. Usually in Risk Meetings executives look for a few things about any risk.
- What is it?
- What is the likelihood of it to occur?
- What is the impact if it does occur?
- What are we doing about it?
- How much does it cost to fix?
However, this isn't a risk approval meeting where we need to go into that level of detail. So, let's keep our cyber risk reporting at an executive level by identifying our top three to five material risks and showing our cyber responses to each risk.
For example, if you believe phishing is your number one cyber risk, then highlight it and talk about how you have created a phishing education program that lowers click rates and increases phishing reporting to the Cyber Incident Response Team. When phishing attacks are reported, your team has a Service Level Agreement (SLA) to respond to phishing reports within four hours to minimize any potential harm. You can also highlight that your organization also has email protection tools in place such as Proofpoint that stopped thousands of phishing attacks during the last quarter.
In summary you are acknowledging that your company has Cyber Risks which can harm the organization. You are protecting the organization the best you can given the resources available to your team. If someone doesn't like your four-hour SLA, then you might offer up that you could decrease the response time to a one-hour SLA if you had one additional headcount. This creates a business decision to give you additional headcount, which is a great discussion to have.
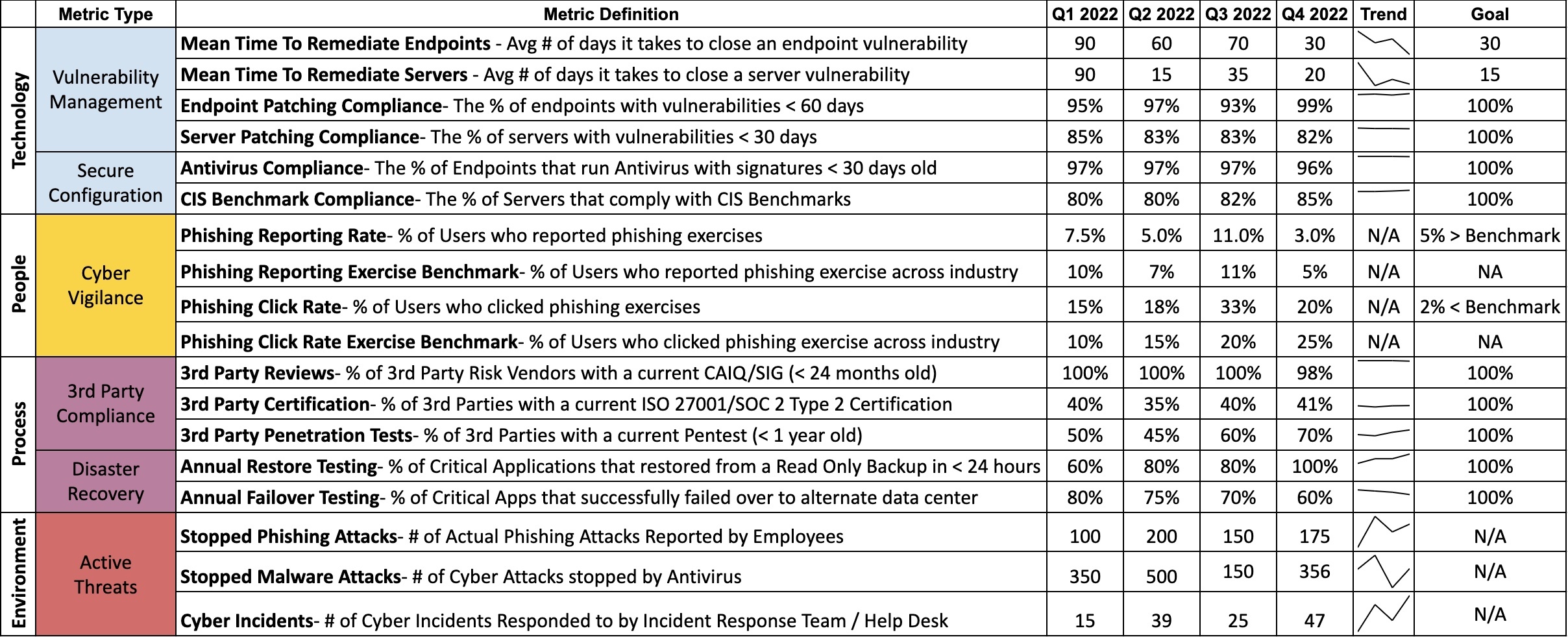
Once you have talked about the top three to five risks your organization faces, we recommend talking about key metrics to measure the Cyber Program. You could call these the metrics that matter. Essentially, they are tactical metrics that you measure month to month because they show risks that could result in major cyber-attacks. Our favorite place for metrics that matter is the OWASP Threat and Safeguard Matrix or TaSM (pronounced like Tasmanian Devil). Please note we have a link to it in our show notes. Please, please, please read about the OWASP Threat and Safeguard Matrix. It's a short five-minute read, and you will be glad that you did.
What does the Threat and Safeguard Matrix teach us about cyber metrics? It says all good metrics show a status, a trend, and a goal.
- Status shows where we are right now
- Trends show if the project, program, or company is getting better or worse
- Goals show the end state so we know when we are done and if we should be happy with our current progress
The OWASP Threat and Safeguard Matrix then categorizes cyber metrics into four major areas: technology, people, process, and environment.
- Technology-based metrics show things like how fast we are patching devices and how well are our servers and laptops configured. Think about it, if you have servers that are internet-facing which are not patched then it's just a matter of time until bad actors will cause your company (and you) a really bad day. This isn't something that you can wait on. So, your organization needs to continually track progress and burn these numbers down as quickly as possible. So, let's do something about it. Start by looking at your company's security policy that defines the patch timelines for high and critical vulnerabilities. It might say something such as we require critical vulnerabilities to be patched in 15 days and high vulnerabilities to be patched in 30 days. From that security policy you create a Service Level Agreement for the IT department to meet. So, you measure the percentage of your servers that have zero high and critical vulnerabilities greater than that 15 or 30-day window. Yeah, it's going to look terrible in the beginning when your IT department shows that only 30% of its servers are patched according to the enterprise service level agreements. But transparency brings reform. When the CIO sees that these metrics are routinely being briefed to the CEO and executive leadership team, then things will change. The CIO will say "not on my watch" and usually lead the IT team to make the changes needed to improve patching.
- Another metric category we see from the OWASP TaSM is People. When we think about cyber threats to people we usually think about phishing. So, during your monthly phishing exercises record your click rates and your reporting rates. Since each phishing exercise is different you should benchmark your organization against other organizations who took the same phishing exercise. You can say we had 5% click-through compared to our industry vertical that scored 7%. If you are doing better than your peers, then you can show you are following best practices and meeting the legal term of due care. These metrics might lower your cyber insurance costs. These metrics could also be extremely helpful if your company were sued as a result of a data breach that begin with successful phishing attacks. So, measure them each month and make good progress.
- The third metric category is Process-based metrics. Here you can monitor things like your third-party risks by looking at your processes that track how many of your third parties pass a review, have active ISO 27001 or SOC 2 Type 2 reports, and have recently passed penetration tests. Another process you might look at is what percentage of your critical applications performed adequately during both a Disaster Recovery exercise and a Business Continuity Plan exercise. These metrics are helpful during Sarbanes-Oxley (SOX) attestations and other regulatory reviews.
- The fourth and last metric category defined by the OWASP TaSM is Environment-based metrics. This refers to things outside of your organization that you don't control. Even though you don't control them they can have a substantial impact on your organization. You can think of countries passing new cyber or data privacy laws, regulators asking for new information and compliance activities, and malicious actors and fraudsters taking interest in your company all as examples of environment-based factors. Please don't confuse environmental factors with saving the Earth. This is not the context you are looking for. Environment metrics could be used to show how many legitimate phishing attacks your organization stopped when someone reported a phishing attack, and the Incident Response Team confirmed it wasn't a false positive. Note these are actual phishing attacks not phishing exercises. This is an important metric because it shows that despite email protection tools in place, things got passed it. If you notice a 500% increase in confirmed phishing attacks you might need to buy additional tooling to interdict them. Another metric you might look at is how many reported help-desk tickets your organization responded to that were caused by a cyber incident. These types of metrics can help inform management just how big the malicious attacker threat is and can be used by you to justify additional resources.
Well, that's a good overview on Cyber Metrics that you can look at each month, but we still have two more categories to go over in our cyber update. Remember if you want to learn more on cyber metrics, please look at the OWASP Threat and Safeguard Matrix.
The third broad category of slides to include in your board deck is A Cyber Roadmap that Identifies High Profile Programs and Projects. Executives want to see the big picture on how you are evolving the program. So, show them a roadmap that says over the next three years here is the big picture.
For example, in 2022 we are focusing on improving ransomware defenses by enhancing our backup and data recovery process. We will also improve our ability to prevent malware execution in our environment by adding new Windows group policies.
In 2023, we will shift our focus towards improving our website security. We will be launching a bug bounty program that allows smart and ethical hackers to find vulnerabilities in our websites before malicious actors do. We will be upgrading our Web Application Firewall after we finish our three-year contract with our current vendor. We will also be adding a botnet protection tool to our internet-facing websites given the recent attacks we have been experiencing.
In 2024, we will then shift our focus to improving our software development process. We will be purchasing a tool to gamify secure software development amongst developers. This should lower the cost of vulnerability management. We will also be building custom courses in house that teach developers our company's requirements to build, test, and retire applications correctly.
When you present this type of Cyber Roadmap you might show a single slide with a Gantt chart view of when high profile projects occur with the executive summary of the points previously mentioned.
The last major category is a Cyber Maturity Assessment. Essentially you want something that independently measures the effectiveness of the entire Cyber Program. For example, many organizations use the NIST Cybersecurity Framework, ISO 27001, the FFIEC Cyber Assessment Tool, or HiTrust to benchmark their program. Consider hiring an independent auditing company to measure your organization's security maturity. You will get something that says here's the top fifteen domains of cyber security. Today, on a scale of one to five, your organization measures between a two and four on most of the domains. Most companies in your same industry benchmark are at a level three compliance so you are currently underperforming vs your peers in four domains. You can take that independent assessment and say we really want to improve all level two scoring opportunities to be at least a three. This can be something you show in a spider graph or radar chart. You can show the top five activities needed to improve these measurements and provide timelines for when those will be fixed. This shows the executive leadership team that security is never perfect, how you benchmark against your peers, and provides them with the same confidence that they would get from an audit to confirm you are working effectively.
So, let's summarize.
We talked about Herzberg's hygiene factors, things that aren't perceived as satisfactory when present but are dissatisfactory when absent. Remember, satisfaction and dissatisfaction are not opposites. The opposite of dissatisfaction is no dissatisfaction.
That helps us understand that when briefing management, we will not be able to delight them with the overall state of our cybersecurity program, but we can cause them not to worry about it. Focus on risk reduction, and how your program is helping your organization work toward that goal.
We talked about why we need to brief management and how often. Different regulations require executive teams to articulate a cybersecurity strategy and empower the appropriate individuals to execute it. In addition, most rules require at least annual security briefings; you may want to strive for more frequent meetings to keep your leadership team well-informed.
Your goal is to have your board set the security culture from the top and hold C-level executives accountable for funding and maintaining cybersecurity initiatives.
We covered the four things you should include in your executive briefings: cyber risks and responses, cyber metrics, a cyber roadmap that identifies high-profile programs and projects, and a cyber maturity assessment.
By addressing risk in multiple forms, showing that you can measure and track your progress toward your security goals, that you have a solid plan for the next couple of years, and that you can demonstrate your maturity relative to peer companies, you will go a long way toward keeping your board happy, or more precisely, not unhappy.
Lastly, don't forget to look up the OWASP TaSM model. It's a really useful tool for mapping threat categories to the NIST cybersecurity framework and showing where you may have gaps in your program (represented by blank cells in the matrix.) The link to that is in our show notes.
Well, we hope that you have enjoyed today's episode on Updating the Executive Leadership team on the Cyber Program and we thank you again for listening to us at CISO Tradecraft. Please leave us a review (hopefully five stars) if you enjoyed this podcast and share us with your peers on LinkedIn. We would love to help others with their cyber tradecraft.
Thanks again and until next time, stay safe.
References
-
https://www.mindtools.com/pages/article/herzberg-motivators-hygiene-factors.htm
-
https://threataware.com/a-cisos-guide-to-cybersecurity-briefings-to-the-board/
- https://www.spencerstuart.com/-/media/2021/october/ssbi2021/us-spencer-stuart-board-index-2021.pdf
-
https://www.spencerstuart.com/research-and-insight/cybersecurity-and-the-board
- https://www.sec.gov/investment/im-guidance-2015-02.pdf
-
https://proteuscyber.com/privacy-database/ny-dfs-section-50004-chief-information-security-officer
Comments (0)
To leave or reply to comments, please download free Podbean or
No Comments
To leave or reply to comments,
please download free Podbean App.